For suppliers to the MOD, the Cyber Security Model (CSM) was rolled out to large suppliers from January 2017 – with the full launch in April 2017.
To determine the Cyber Risk Profile in all MOD contracts, the MOD completes a Risk Assessment (RA) for each MOD contract. DEFCON 658 must be included in all MOD contracts with a Cyber Risk Profile higher than ‘Not Applicable’. Where contracts contain DEFCON 658, tenderers are required to complete a Supplier Assurance Questionnaire (SAQ) as part of their tender response and, if awarded the contract, the SAQ must be renewed annually by the supplier. RAs and SAQs are completed on MOD’s Supplier Cyber Protection Service (SCPS) tool (aka “Octavian”).
To comply with the CSM requirements, the MOD supply chain will need Cyber Essentials or Cyber Essentials Plus and have information security governance policies in place. The Department of Business, Innovation and Skills (BIS) introduced the Cyber Essentials (CE) scheme in April 2014 and mandated that suppliers to the public sector achieve certification under the scheme for many Government contracts from October 2014.
Ascentor strongly recommends that defence industry companies prepare for CSM by gaining certification to Cyber Essentials in advance – so they are ready to respond to contract requirements. In our experience, the larger the business, the more complex and time-consuming the process. Don’t delay and put future contracts at risk.
The following article will tell you more about the CSM.
What is the Cyber Security Model (CSM)?
The Defence Cyber Protection Partnership (DCPP), which comprises MOD representatives, 13 prime suppliers and defence industry trade bodies, was established in 2012 with the aim of improving cyber security maturity for the community.
The DCPP felt that the CE scheme did not represent a broad enough degree of security because, at the time, it only covered five major technical security controls and did not include wider aspects such as governance and risk management. It therefore developed the CSM as its own standard for supplier cyber security, based upon the CE scheme, but with some additional control requirements.
The CSM will enable government procurers to mandate proportionate cyber security standards from suppliers, appropriate to the level required for a particular contract.
Why does it matter?
The importance of the security of defence information in the supply chain cannot be underestimated – it is a topic that Ascentor cares passionately about. Security breaches have the potential to put lives at risk, wreak havoc and bring down businesses. At the same time, cyber-attacks are becoming more and more sophisticated. Even if you feel your current security measures are robust, you will always be at risk of a cyber attack if you operate in the defence industry. In this climate, CSM has been designed to strengthen supplier cyber security.
How does it work?
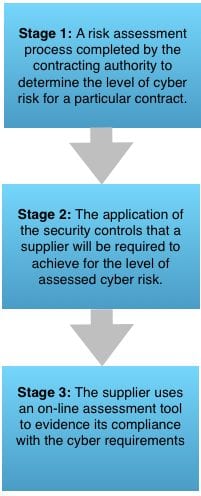
The Stage 1 risk assessment is completed by the contracting authority and is based around a questionnaire.
The output of the questionnaire determines the level of risk and complexity of the project using a grading of five Cyber Risk Levels: Not Applicable, Low, Medium, High, Very High.
Whilst there are statements of threat for each of the Cyber Risk Levels, there is no specific correlation between them and the Government Security Classification scheme.
In Stage 2, the contracting authority decides upon the Cyber Risk Level for a particular contract and the supplier implements the appropriate Cyber Risk Profile as per the table below:
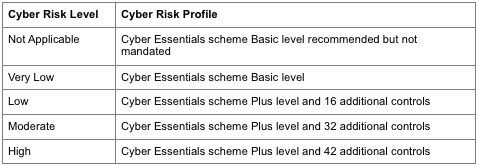
Profiles in the Cyber Security Model: cyber risk profiles’ requirements.
The controls in the Cyber Risk Profiles are the minimum that will be required. There may be occasions when additional controls will need to be implemented; in these circumstances an MOD Cyber Defence and Risk (CyDR) representative will work with the stakeholders.
Stage 3 is the submission of evidence by the contractor, and its review and acceptance (or otherwise) by the contracting authority. An on-line tool is being developed and this will allow companies to input their evidence so that it can be assessed and certification issued. The tool will also automate the Stage 1 process and map the tiers of the supply chain for contracts.
How will it affect me?
If your company supports MOD contracts, then you will be required to comply with the CSM There has not been a statement on whether the CSM will be applied to legacy systems, but it is believed to be unlikely. Importantly, the CSM will be applied to individual defence contracts.
How do you achieve Cyber Essentials – and what does it cost?
Full details of Cyber Essentials and Cyber Essentials Plus can be found in Ascentor’s Guide to Cyber Essentials. It’s available as a free download – please click the icon below.

Cyber Essentials certification is achievable through an official certifying body and costs £300. Ascentor was selected by IASME as the first licensed external assessors of its Cyber Essentials assessment process and can partner with your organisation to ensure you meet this security management standard.
There’s an additional advantage in achieving certification via Ascentor and IASME. When an organisation with a turnover under £20 million achieves self-assessed certification covering their whole organisation to the basic level of Cyber Essentials, they are automatically awarded Cyber Liability Insurance.
What next?
At Ascentor, we think that the CSM is a positive move. While it is a pity that the CSM is another standard that needs to be understood, interpreted and implemented, we strongly recommend that defence industry companies get ahead of the game by gaining certification to CE so they are ready to respond to the new contract requirements. We can help you achieve CE.
For further information
Follow the Ascentor blog and our Newsletter, and we will keep you informed.
We hope you found this article interesting and helpful. If you need any further guidance on CSM, or any aspect of Cyber Security please contact Dave James at Ascentor.
Email [email protected]










