For suppliers to the MOD, change is coming. The planned rollout of CSM in August of 2016 has been delayed. We are now expecting the Cyber Security Model (CSM) to be rolled out to large suppliers from January 2017 – with a full launch by April. FATS (a commercial MOD framework) will also go live in April and it is expected to include the contractual aspects of CSM.
To be compliant with the requirements of the CSM, the MOD supply chain will need Cyber Essentials or Cyber Essentials Plus and have information security governance policies in place.
Ascentor strongly recommend that defence industry companies prepare for CSM by gaining certification to Cyber Essentials in advance – so they are ready to respond to the new contract requirements. In our experience, the larger the business, the more complex and time-consuming the process. Don’t delay and put future contracts at risk.
For assistance on any aspect of CSM or Cyber Essentials, please contact Dave James at Ascentor [email protected]
The following article will tell you more about the CSM.
In August 2015, Ascentor first highlighted the proposals from the MOD to manage the risk to its information from supply chain companies by introducing the Cyber Security Model (CSM). The CSM is a methodology to assess the cyber risk for individual contracts, which then mandates that suppliers meet a consistent standard of cyber security.
To update our coverage of CSM, we look at recent developments ahead of the planned rollout, now expected at the end of July 2016.
What is the CSM?
MOD issued Defence Standard 05-138 in May 2015 to outline the CSM model and this model has been developed (and is being rolled out) by the Defence Cyber Protection Partnership (DCPP).
MOD is doing this in response to the HMG Procurement Policy Note (09/14) which made it a mandatory requirement for suppliers to the Government of certain types of contracts to hold Cyber Essentials certification .
The MOD had an initial exemption but is now introducing Cyber Essentials, bringing it in-line with other Government departments. As a precursor to this it is implementing the CSM.
The CSM process
The CSM is a three stage process starting with a risk assessment and is covered in more detail in our original article .
The risk assessment stage is completed by the contracting authority and is based upon eight questions to determine the level of cyber risk for the contract. There are four cyber risk profiles and one “Not Applicable” level:

For each cyber risk level there is a defined set of requirements and these can be summarised as follows:
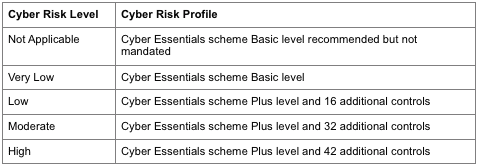
The published set of cyber risk profile requirements give greater detail on the additional controls required at each level and the type of evidence required.
Once a cyber risk level has been defined the supplier (and its supply chain) are required to demonstrate that they are meeting the risk profile requirements. This can be done by showing evidence of certification for the CE and CE Plus scheme as required.
For those cyber risk levels where there are additional security requirements (LOW and above) a Supplier Assurance Questionnaire (SAQ) is being developed by NQC Ltd (the company that produced the HADRIAN tool) and this is planned to be made available via a web portal to which suppliers will be given an account. Suppliers will complete the SAQ and the results will be assessed.
How have things moved on?
As can be seen, the basic requirement is that companies achieve the Cyber Essentials scheme Basic certification. This has been mandated by MOD from January 2016 in a letter from the Defence Commercial Head of Policy, Process and Procedures (P3) on 25 Nov 15 to MOD suppliers and also in Industry Security Notice Number 2016/01:
“For all new requirements advertised from 1st January 2016 which entail the transfer of MOD identifiable information from customer to supplier, or the generation of such information by a supplier specifically in support of the MOD contract, MOD will require suppliers to have a Cyber Essentials certificate by the contract start date at the latest, and for it to be renewed annually. This requirement must be flowed down the supply chain.”
MOD identifiable information is defined as: Information which could be identified as relating, either explicitly or implicitly, to the MOD and its activities.
The CSM is planned for roll out in August 2016 in a phased approach and this will require that contracts with a cyber risk profile above LOW will need certification to Cyber Essentials Plus (as a minimum). Accordingly suppliers are advised to think about achieving that level straight away. It should be noted that the Cyber Essentials certification has to be reviewed annually.
The DCPP has also said that a Cyber-Security DEFCON will be incorporated into all new MOD contracts from 4th April 2016 and that the CSM will become an integrated element of the MOD’s existing Acquisition System Guidance (ASG). It will be mandated at all stages of MOD acquisition, through contracts and supporting documents.
FAQs
The DCPP web site has a lot of very useful information on the CSM and its FAQs document addresses some of the concerns that suppliers may have. Some of these FAQs are paraphrased here:
Q: Does this mean I need to have achieved Cyber Essentials by 1 January 2016?
A: Although the requirement to achieve Cyber Essentials will be included in new contracts from 1 January 2016, compliance is only required by the time of contract award.
Q: If a supplier subcontracts out elements of the contract, does it need to flow this down the supply chain?
A: Yes, the requirement to achieve Cyber Essentials certification should continue to flow down the supply chain wherever those contracts include MOD identifiable information. It is the always the responsibility of the contracting organisation to ensure that its subcontractor has achieved certification.
Q: Can a potential supplier be excluded from the bidding process if they do not have Cyber Essentials certification?
A: As long as a supplier has confirmed it is working towards achieving Cyber Essentials and will have it in place prior to contract award, it will not form part of the selection criteria.
Q: What if a supplier cannot obtain Cyber Essentials ahead of contract award?
A: The MOD will, at its discretion, allow suppliers extended time to obtain the certification if they can prove it is due to delays in achieving certification and not due to a supplier failing the process.
Q: What if a supplier is refusing to comply?
A: It is at MOD’s discretion not to take a company any further in the bidding process for non-compliance with Cyber Essentials.
For those companies that already have either existing requirements such as accreditation, List X assessments, ISO27001 certification or IASME certification, then these will provide additional assurance but still mean that the CSM certification process must be completed.
Issues to be resolved
There are a number of aspects of the CSM rollout that are still being worked on by the DCPP team, and these include:
Q: How far down the supply chain does the CSM have to be applied?
A: This has not been determined yet and will probably be on a case-by-case basis to be agreed with the contracting authority.
Q: Who will review and assess the SAQs for a particular contract on an initial and ongoing basis?
A: This has not been determined yet but is thought likely to be the contracting authority. It is not clear if the Defence Accreditation and Information Security (DAIS) team has a role to play in the CSM process or not.
Q: If a supplier has a poor SAQ response (or indeed has not responded at all) what action will be taken and by whom?
A: It is not apparent who will follow up on SAQ responses or what authority they will have to ask for improvement.
What are the timescales?
Formal rollout of these cyber-security measures in all new Defence contracts is planned to start in August2016. It is likely that these measures will be applied to some existing contracts where they are considered particularly vulnerable to cyber threats.
Before that, three things must be completed: further pen-testing of the risk assessment and SAQ, the development and testing of the automated tool to gather and store data, and the agreement of a supporting commercial framework.
How can we help?
We are an authorised certification body and can conduct a CES and CSM gap analysis. We strongly recommend that defence industry companies get ahead of the game by gaining Cyber Essentials certification so they are ready to respond to the new contract requirements.
For more details about our routes to certification, please see Cyber Essentials Certification with Expert Support.
For further information
We hope you found this article interesting and helpful. If you need any further guidance on CSM or any aspect of Cyber Security please contact the team at Ascentor.










