Originally published in August 2016, this article has been fully updated in November 2020 to reflect changes in Supply Chain Cyber Security. We cover the growing importance of a resilient supply chain and more rigorous application of the UK Cyber Security Model (CSM) and the US Cybersecurity Maturity Model Certificate (CMMC).
In the first part of this blog we created a scenario of just how easy it is to cause a cyber security breach. “Brian” was a contractor with access to the server room. In moments he’d been able to gain access and steal his client’s intellectual property – all without trace. There was a weak link in their supply chain cyber security which he’d found no trouble to exploit.
In Part 2, we introduce a 4-step supply chain cyber security process – and provide links to guidance on supply chain risks and methodologies for assessing an organisation’s security. We also discuss how far down the supply chain you need to manage.
In the first article, we considered that supply chain cyber security is about ensuring that critical information and business performance, relied upon by a company or organisation, is not compromised or disrupted by the companies supporting it.
In practice, this can be a real challenge – as our earlier scenario demonstrated. As was shown in the first blog, most businesses have outsourced some critical functions such as IT, HR or payroll to external service providers. All of these functions contain information that is important to a company and by giving control to an external body (like “Brian” and his employer), the protection of that information, for which the organisation is responsible, has been given to someone else.
Does this matter? Yes, because:
- IT systems provide access to internal networks, storage systems, databases and devices that hold sensitive company and customer information
- HR systems contain personal information about staff
- Payroll and finance systems contain details of company finances, bank account details and staff personal information
- And also because of trust. A supply chain is effectively a team and as human beings, we inherently trust other team members. Compromising a link in the chain, compromises the team
This information could be:
- Exposed to the wrong people
- Be adulterated or destroyed
- Made vulnerable to malware (i.e. ransomware) or hacking, causing disruption to your business and the inevitable costs and delays involved in putting things right
- Used as a cover to compromise the security and integrity of a larger, higher-value target/member of the supply chain
Even ignoring apocalyptic scenarios like ransomware (which no-one thinks is ever going to happen in their company!) you are legally liable for the security for personal information under the Data Protection Act so it needs to be protected – even if another company is actually “hands-on” with it.
So if you feel that “something” should be done to manage your supply chain cyber security where can you start?
Supply Chain Cyber Security – a four-step process
Here is a basic four-step process that you could consider:
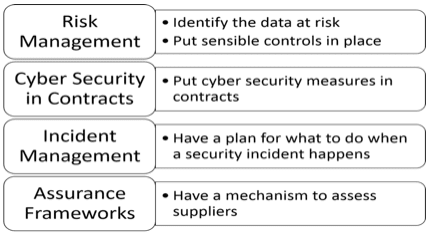
Step 1: Risk Management
- Know what services you have outsourced. (This sounds bizarre but many companies don’t know exactly).
- Know if each contract involves any sensitive information or functions that are critical to your business (like IT support).
- For each such contract carry out a simple risk assessment of what happens to your business if the information is compromised, corrupted or destroyed or the critical function fails.
- If sub-contractors are involved, understand what information they will have and how they will store, process and access the data provided to them.
- Think of things like remote access security, Bring Your Own Device (BYOD) usage and physical security.
- Ask what assurances the supplier can provide that they are keeping the data secure.
- Establish if supplier assurances are within your risk appetite. If not, provide specific detailed security requirements and conduct your own assessment of how well they are implemented.
- Decide what you can realistically do to prevent security issues happening in the first place and to reduce the consequences if they do happen. (You can’t get rid of risk completely but at least you will know what it is).
Step 2: Include Cyber Security in contracts with suppliers
- Be an intelligent customer and have security requirements in contracts. (Don’t be adversarial but specify clearly what you expect as part of the service).
- Have a supplier on-boarding process that includes a high-level assessment of company security.
- For contracts involving personal data, define the roles of data controller and data processor.
- Include supplier contracts within the scope of any Cyber Insurance that may be in place. Incident management may need to widen the scope further than just your own company.
- Specify what is expected from all parties in the event of service failure.
Step 3: Incident management
- Include supply chain incidents in your own incident management plan.
- Work with suppliers to confirm that they have an incident management plan and that it can align with yours. (Work with suppliers to get the right answer for both of you).
- Have a clear understanding of which organisation has what responsibility in the event of an incident.
Step 4: Assurance frameworks
- Have a mechanism to assess the security of each supplier. Have maturity levels for continuous improvement.
- Understand what security is needed for the business and avoid “box ticking”.
- Use existing certifications such as ISO27001 or Cyber Essentials/Cyber Essentials Plus.
- Make security requirements clear and above all, relevant and achievable.
- Work with suppliers where there are deficiencies. Don’t forget a supply chain is a team.
Government and larger organisations are looking at ways to understand and manage supply chain risks and there’s a number of methodologies to both assess risks and to assess the maturity of supply chain companies.
Guidance on supply chain risks can be found from: NCSC, CPNI, Carnegie Mellon University, ISO28000, the Information Security Forum and the National Institute for Standards and Technology (NIST).
Methodologies for assessing an organisation’s security include: the Information Assurance Maturity Model and the ISF Supply Chain Information Risk Assurance Process (SCIRAP).
There are tools for assessing supply chain risks and these include: Hadrian, NIST, CDCAT, Rizikon and Cyberwiser. The MoD proposes to deploy a tool based upon Hadrian that will assess and report on the maturity of all its suppliers.
How far down the supply chain do you need to manage?
The realistic answer is “it depends” because it is a matter of how far down the supply chain the information you care about goes. Some requirements such as the CMMC and the CSM are explicit on this point.
So how does all of this help? Well, considering the scenario in Part 1 of this blog of Brian the outsourced IT provider stealing proprietary information, what could have been done differently?
- The risk of outsourced IT could have been recognised and additional security controls put in place such as:
- No unescorted or out-of-hours access for contractors.
- Technical controls to prevent unauthorised USB devices on servers.
- Logging and audit mechanisms to detect unauthorised access and/or data download.
- Brian’s company could have been assessed to confirm that its personnel security measures were robust enough to avoid employing “Brians”.
- Brian’s company could have been made liable for his actions (if detected).
Supply chain cyber security is a very real issue for companies. If you are going to understand and manage the risks to the information you care about this aspect must be included. As ever, it is largely common sense – where is the information, what are the risks and what can you do about them?
And, as we have been highlighting in our other blogs, this is not an issue restricted to large, multi-national companies. It is hugely relevant to Small and Medium businesses as well. If anything, Small and Medium size enterprises are a more readily accessible target and a perfect “way in” to larger supply chains.
If you need guidance on how to assess your supply chain risks Ascentor can help.










